Crocodile Writeup
Overview
For this machine, I started with an nmap scan. Port 21 and Port 80 are open and we can also see the services (and version) each port runs.
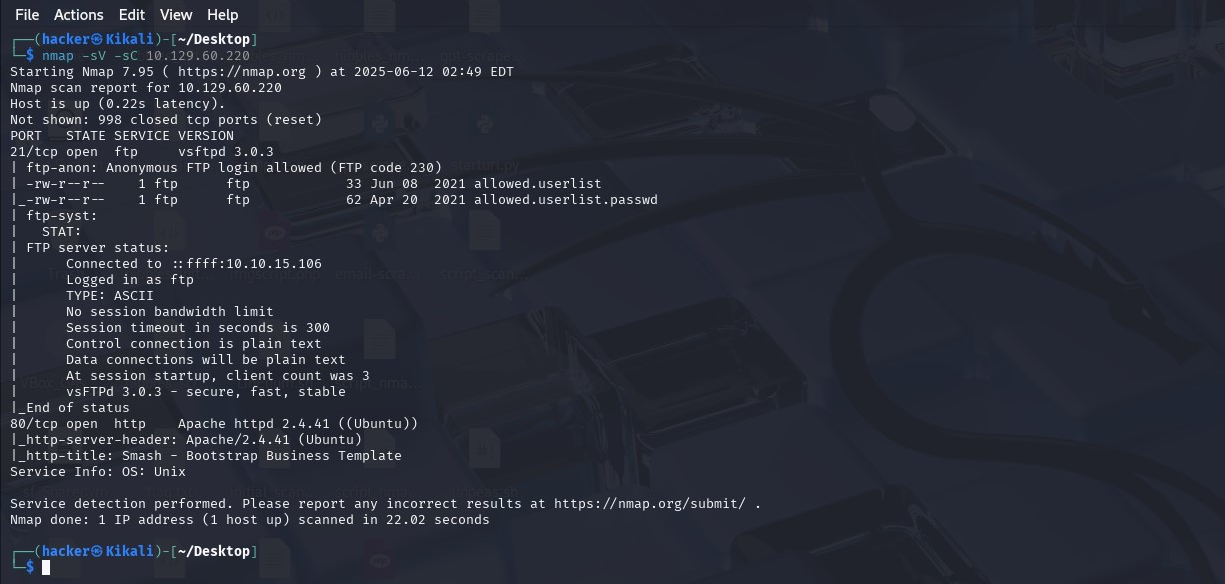
Crucially, this server allows ftp anonymous login, which is fantastic!

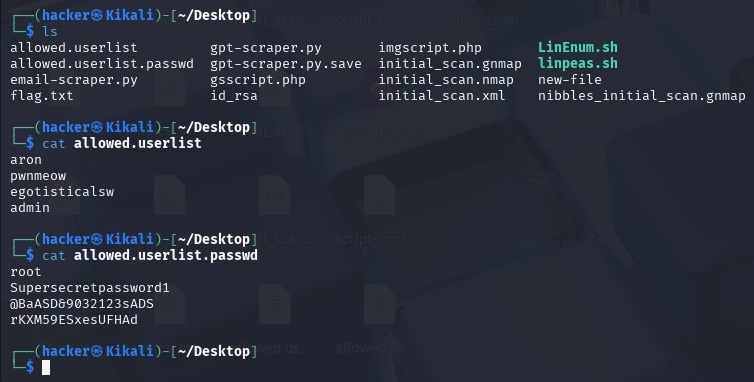
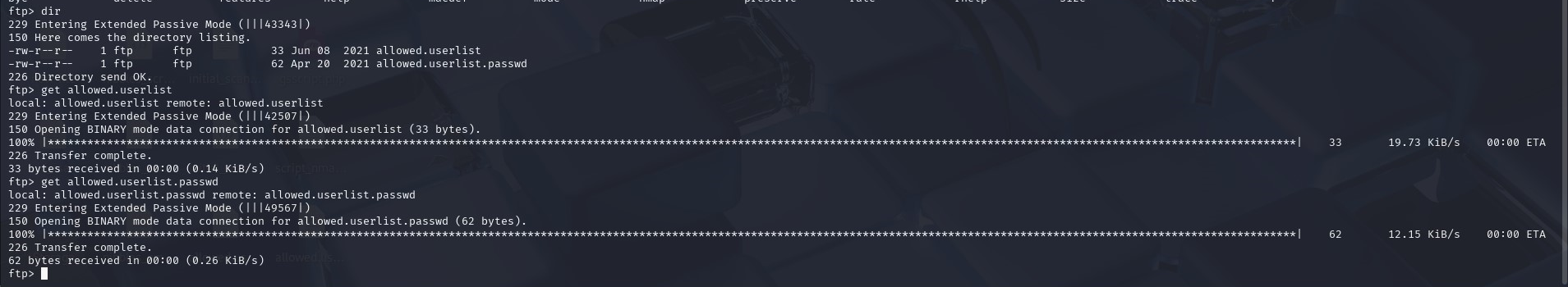
Now that we’ve logged in, let’s explore the system and retrieve the flag. We see two interesting files in our currency directory, which we can download into our machine and view.
The above users and passwords could help us escalate privileges or even log into the HTTP server that we saw open at port 80 (Apache httpd 2.4.41). The web page displayed at port 80 is as shown:
I tried navigating the pages to find any direct path to attacking the server, but it led to nowhere. Even Wappalyzer didn’t help.
Next I attempted to enumerate hidden directories using gobuster (-x filters out unnecessary files). What we’re looking for is an admin panel that can give us a foothold (using the credentials we obtained from ftp).
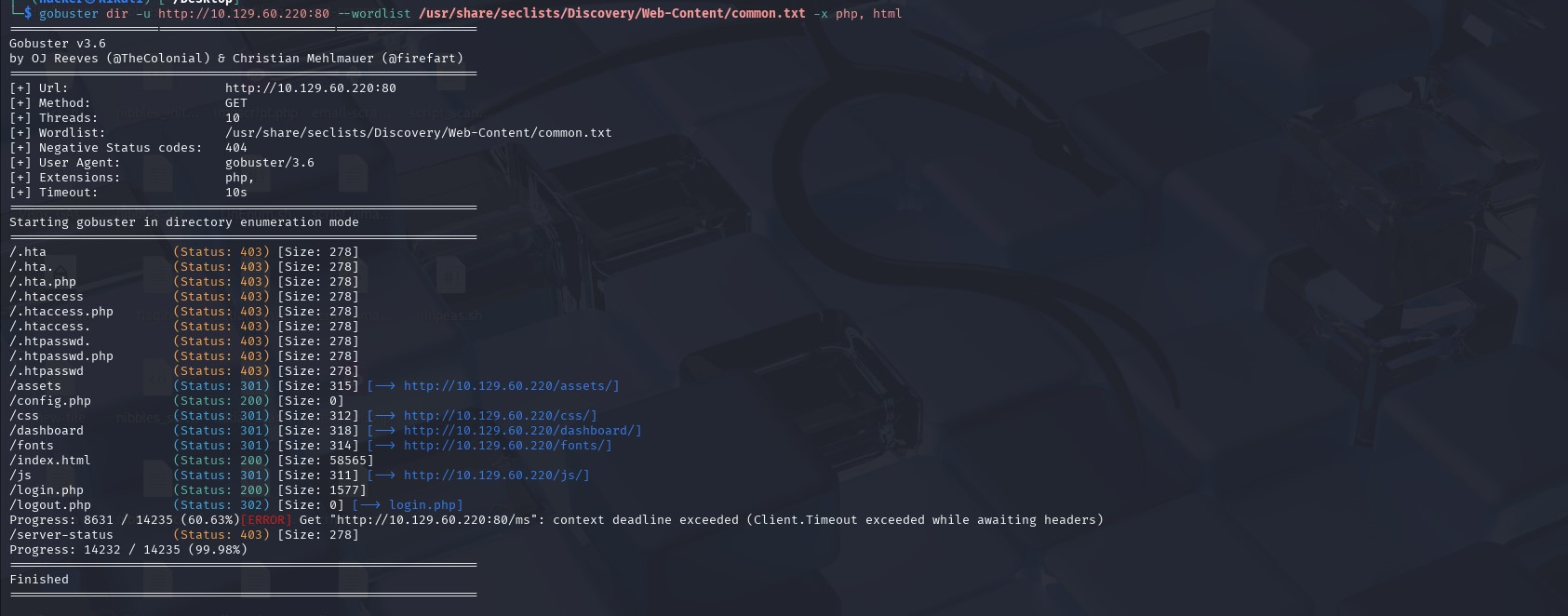
At last, we found a /login.php page. Let’s try to login (luckily only 4 credentials to attempt!)
We’ve managed to login with admin credentials since we can now see a Server Manager admin panel.
Let’s retrieve the flag