Appointment - HTB Catch the Flag
Overview
Appointment is a (very easy) target machine containing a back-end database that is vulnerable. My goal is to attack it with SQL Injection.
Skills Learned
- Web enumeration
- SQL Injection
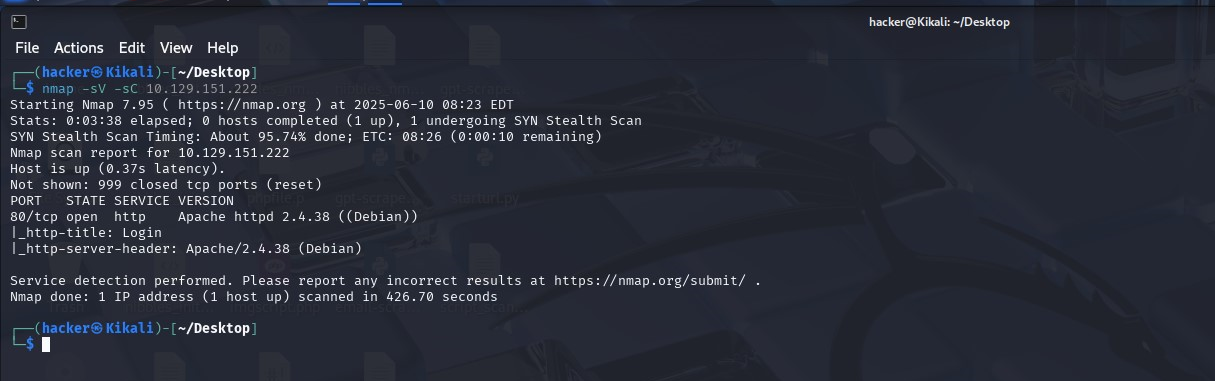
Ports enumeration
First we start with an nmap scan to find open ports. We see that port 80 is open and it’s running Apache 2.4.38.
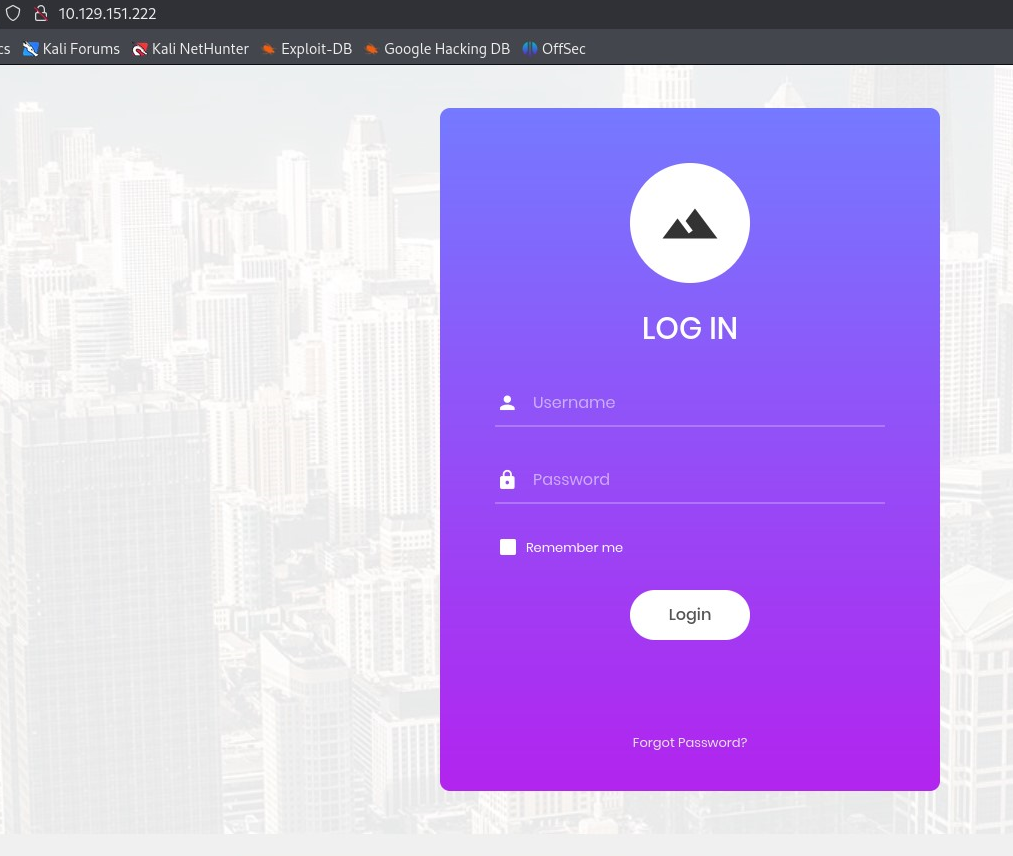
Let’s see the web server on a browser. And it’s a login page. Now the next goal is to find the login credentials.
I tried a brute-force attack using gobuster to find hidden web directories but nothing interesting came up.
Next I tried to login by manipulating input credentials through SQL Injection. If the SQL database is misconfigured (i.e no input validation), we can comment out (#) the password of the admin and see if it bypasses the login. And it does!
(The admin’# will search for the admin username but comment out the rest of the query, i.e password).
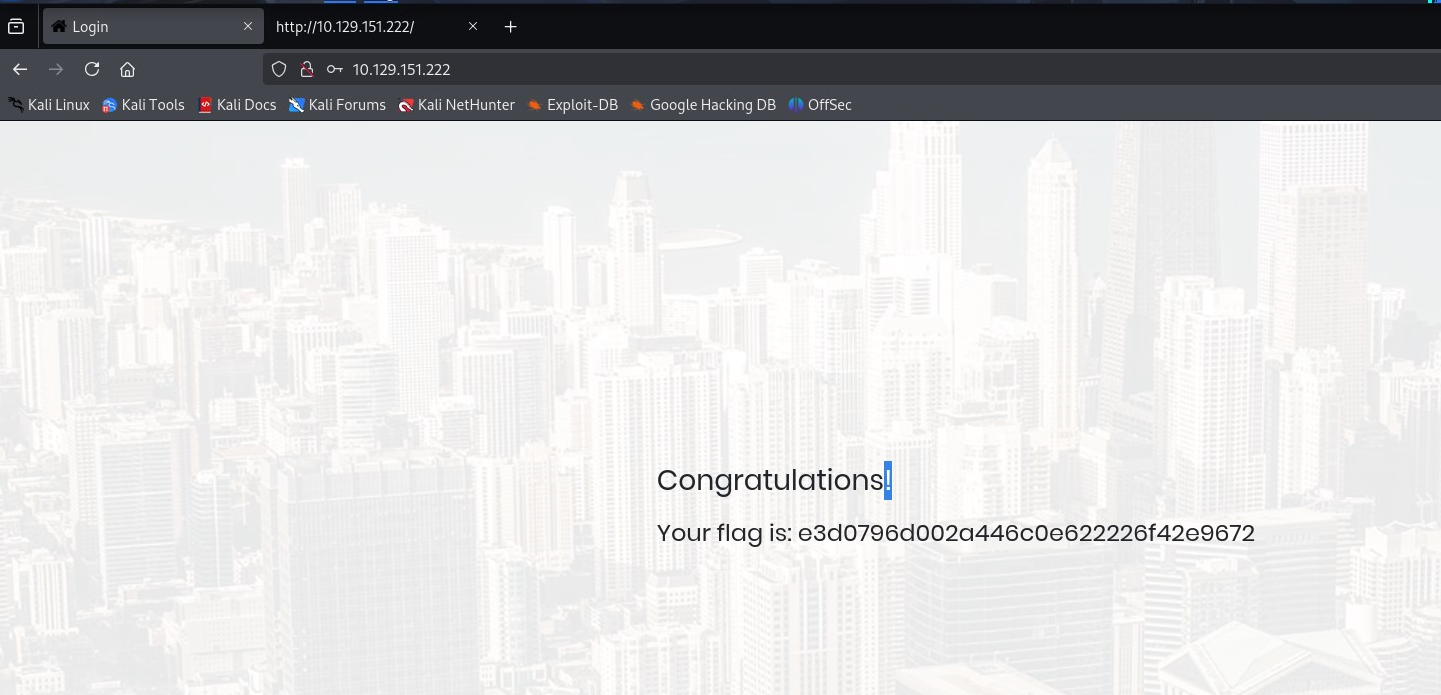
Now we see the flag